Hashing is a fundamental concept in computer science and cybersecurity, particularly in the realm of password security. It involves the process of converting input data (such as a password) into a fixed-size string of characters, known as a hash value or simply a hash. This hash value is generated using a hashing algorithm, which is designed to be a one-way function, meaning it should be computationally infeasible to reverse the process and obtain the original input from the hash alone.
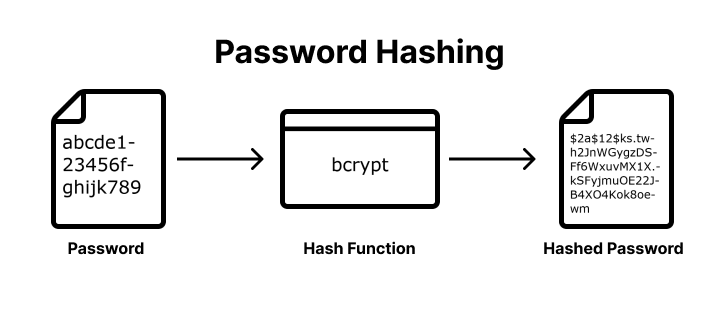
Hashing plays a crucial role in password storage and authentication systems. Instead of storing plaintext passwords, systems typically store hashed versions of passwords. When a user attempts to log in, the system hashes the entered password and compares it with the stored hash. If they match, the user is granted access.
However, the security of hashed passwords can be compromised if an attacker gains access to the hashed values. In such cases, attackers may attempt to decrypt the passwords using various tools and techniques. Some common methods used for password decryption include:
- Brute Force Attacks: In a brute force attack, an attacker systematically tries every possible combination of characters until the correct password is found. While this method can be effective, it is time-consuming and resource-intensive, especially for complex passwords or strong hashing algorithms.
- Dictionary Attacks: A dictionary attack involves using a predefined list of words, phrases, or commonly used passwords to guess the original password. This method is more efficient than brute force, particularly if the password is weak or commonly used.
- Rainbow Tables: Rainbow tables are precomputed tables containing hash values for a large number of possible passwords. Attackers can use rainbow tables to quickly look up the hash of a stolen password and find the corresponding plaintext password.
- Password Cracking Tools: There are numerous password cracking tools available, such as John the Ripper, Hashcat, and Cain and Abel, which automate the process of password decryption using various techniques including brute force, dictionary attacks, and rainbow table lookups.
In conclusion, hashing is an essential tool for password security, but it is not foolproof. Organizations and individuals need to use strong hashing algorithms and implement additional security measures to protect against password decryption attacks. Additionally, users should choose strong, unique passwords to mitigate the risk of successful attacks.