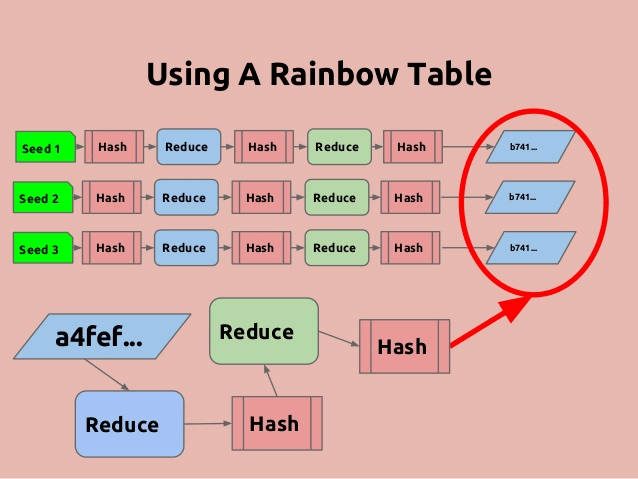
Imagine a treasure chest overflowing with colorful chains, each a link to a secret password. That’s essentially the concept behind a rainbow table attack, a method hackers use to crack stolen password hashes.
Here’s the breakdown:
- Hashed Passwords: Websites typically store passwords not in plain text, but as a scrambled mess of characters called a hash. This makes them unreadable, even if stolen. We have discussed this topic extensively in the previous blog, so refer to those.
- Rainbow Tables: These are precomputed databases containing billions of plaintexts and their corresponding hashes. Think of them as giant dictionaries for hackers.
- The Attack: When an attacker steals password hashes, they compare them against the rainbow table. If a match is found, the corresponding plaintext password is revealed!
Rainbow Table Attack Example (Hypothetical Scenario):
Download a sample rainbow table or create rainbow tables using rainbowcrack
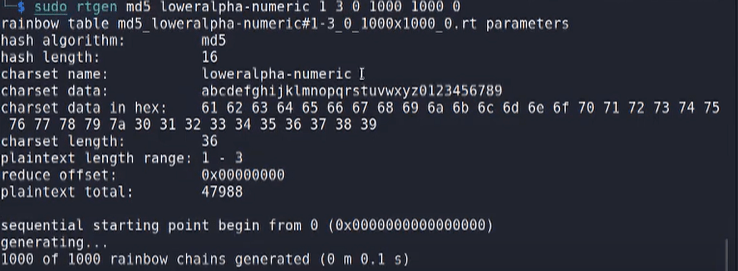
- Sort Rainbow Tables
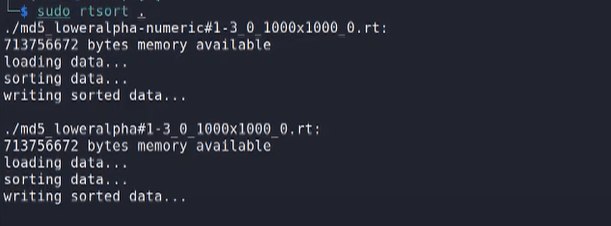
- Obtain the HASH of the password, and identify the hashing algorithm or by using impacket-secretsdump
- Use RCRACK to crack the password
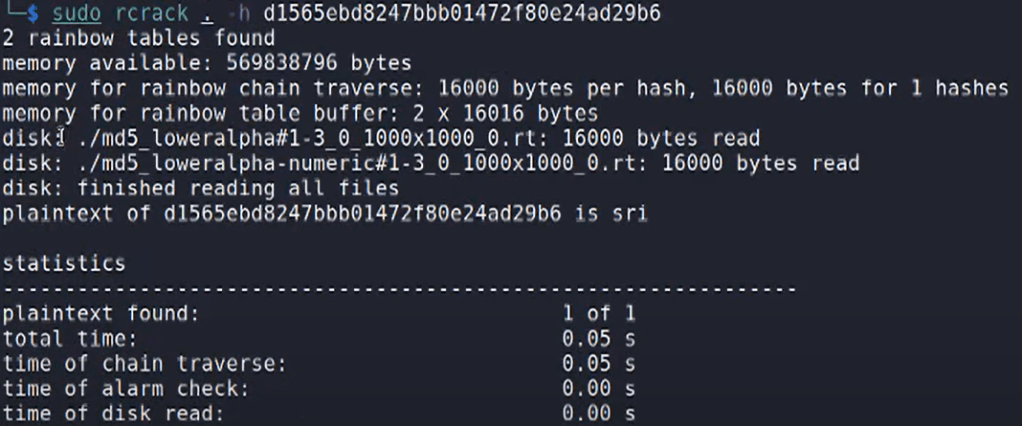
Since hashes are divided into small chunks, it’s easier to crack a hash. But, one drawback of RainbowTables is that it can be quite huge in size.
Key Differences: Rainbow Table vs. Dictionary Attack
Whilst brute force can be easy to understand, as it’s like knocking at the door until it opens. Below are the key differences between rainbow table and Dictionary Attack.
- Precomputation vs. On-the-Fly: Rainbow tables are pre-calculated databases with billions of password-hash pairs. Dictionary attacks try passwords one by one, often using word lists or common phrases.
- Speed: Rainbow tables are much faster if they contain the specific password being cracked. Dictionary attacks can be faster for simpler passwords but slow down for complex ones.
- Flexibility: Rainbow tables are limited to the pre-computed data. Dictionary attacks can be customized with different word lists or rules for password generation.
Analogy:
- Rainbow Table: Like having a giant phone book with every name and phone number. If you have someone’s name (stolen hash), you can instantly find their number (original password).
- Dictionary Attack: Like calling every number in the phone book one by one until you find the person you’re looking for (original password).
Defending Against the Rainbow
Thankfully, there are ways to defend against rainbow table attacks:
- Strong Passwords: Complex passwords with a mix of uppercase, lowercase, numbers, and symbols make it much harder to crack them, even with rainbow tables.
- Salting: Websites add a random string (salt) to passwords before hashing. This creates unique hashes for the same password, rendering precomputed rainbow tables useless.
- Regular Updates: Security practices and hashing algorithms evolve. Keeping software updated ensures the strongest protection available.
- Eliminate passwords: The ONLY way to ensure the prevention of password-based attacks is through eliminating passwords. Without a list of password hashes to steal there is no way to execute a rainbow table attack. Passwordless authentication or MFA
Don’t you wanna know more about Salting
Salting is a security technique used in password hashing to add an extra layer of protection against attackers trying to crack passwords. Here’s how it works:
Imagine spices in your food:
- Plaintext password: The base ingredients of your dish (e.g., chicken, vegetables).
- Hash function: Cooking the ingredients to create a new dish (hashed password).
- Salt: A random spice added before cooking (unique random data).
Why is salt important?
- Unique Hashes: Even if two users have the same password (same base ingredients), adding a unique salt (different spice) creates entirely different hashed passwords (final dishes). This makes pre-computed attacks like rainbow tables ineffective.
- Slower Cracking: Attackers would need to generate a new rainbow table for every single salt value, making large-scale attacks much more difficult and time-consuming.
Salting Example:
- The user creates a password: “password123”
- The server generates a random salt: “!@#salt123”
- Password and salt are combined: “password123!@#salt123”
- This combined string is fed into the hashing function, resulting in a unique hash (unreadable scrambled characters).
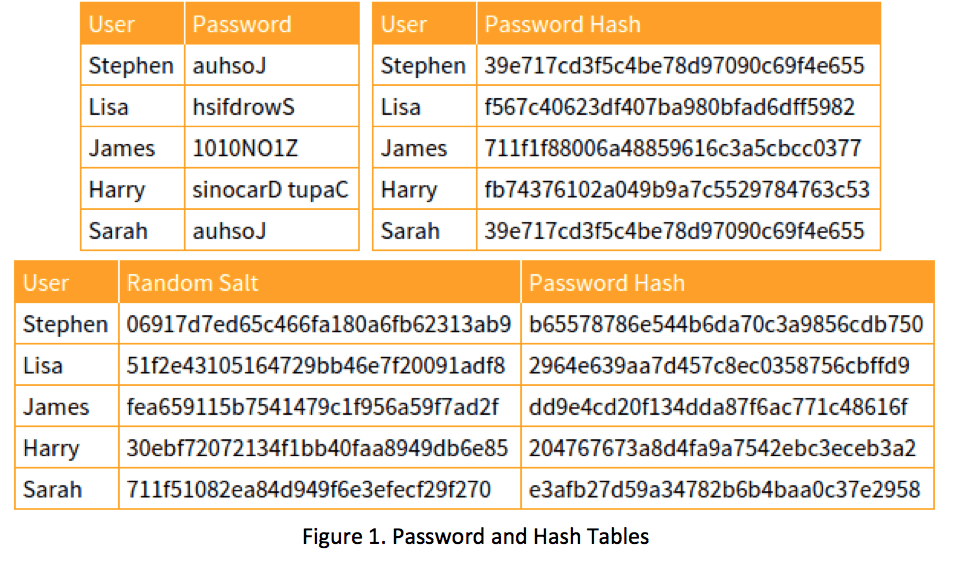
Storing the Hashed Password:
The server only stores the final hashed password (not the original password or salt on its own). This way, even if an attacker steals the hashed password database, they cannot easily reverse the hash to get the original password.
Benefits of Salting:
- Makes rainbow table attacks impractical.
- Protects against stolen password databases.
- Adds an extra layer of security to password storage.
Remember: Salting is a crucial security measure for password protection. When used with strong passwords and proper hashing algorithms, it significantly strengthens your defenses.
To summarize, rainbow tables are an effective way for decrypting hashes, but there are steps such as salting which makes it impossible to decrypt a password. So in the next blog will discuss about a method by which an attacker does not have to decrypt a hash to gain access, interesting isn’t it, stay tuned.